What is PEAKS?
The name is an acronym for Platform for the Efficient Analysis and Secure Composition of Software Components. We solve (or alleviate) the dilemma you are facing when trying to write secure software efficiently using pre-existing software components. Currently, it is pretty hard to limit the libraries you use to the privileges you want to give to them. In a common setting these libraries run with the same privileges as their hosting process and can therefore do all the good and all the harm as the process can.
We would like to change that, because we believe this could be solved better!
How does it work?
Following the Principle of Least Authority, software libraries should only be equipped with the privileges necessary for their job. There are two possible ways to achieve this… You could either isolate the components from the rest of the application and only process those requests that are privileged or you could monitor its behavior and make decisions based on the monitoring.
In PEAKS we follow the latter approach to reach an effective isolation through the monitoring of static properties. We analyze Java libraries and try to find transgressions of the Object-Capability Model. In the OCaps Model objects in an object-oriented system are both the subject and the privilege of the security system. Or better: they could be used in either way. Here the privileges – called capabilities – only can be transferred from one subject to the other in four ways:
- The initial setup of the system is granting it
- Parenthood – a new object is created. The creator owns the capability to call the object.
- Endowment – during the creation of and object the creator endows the newly created object with a subset of its own capabilities.
- Introduction – when an object calls another, it can choose to transfer the capabilities to the other object.
It is obvious that some widely used object-oriented programming models such as Java can violate this principle. Though static analysis we try to find these transgressions in libraries. They can be of the following types.
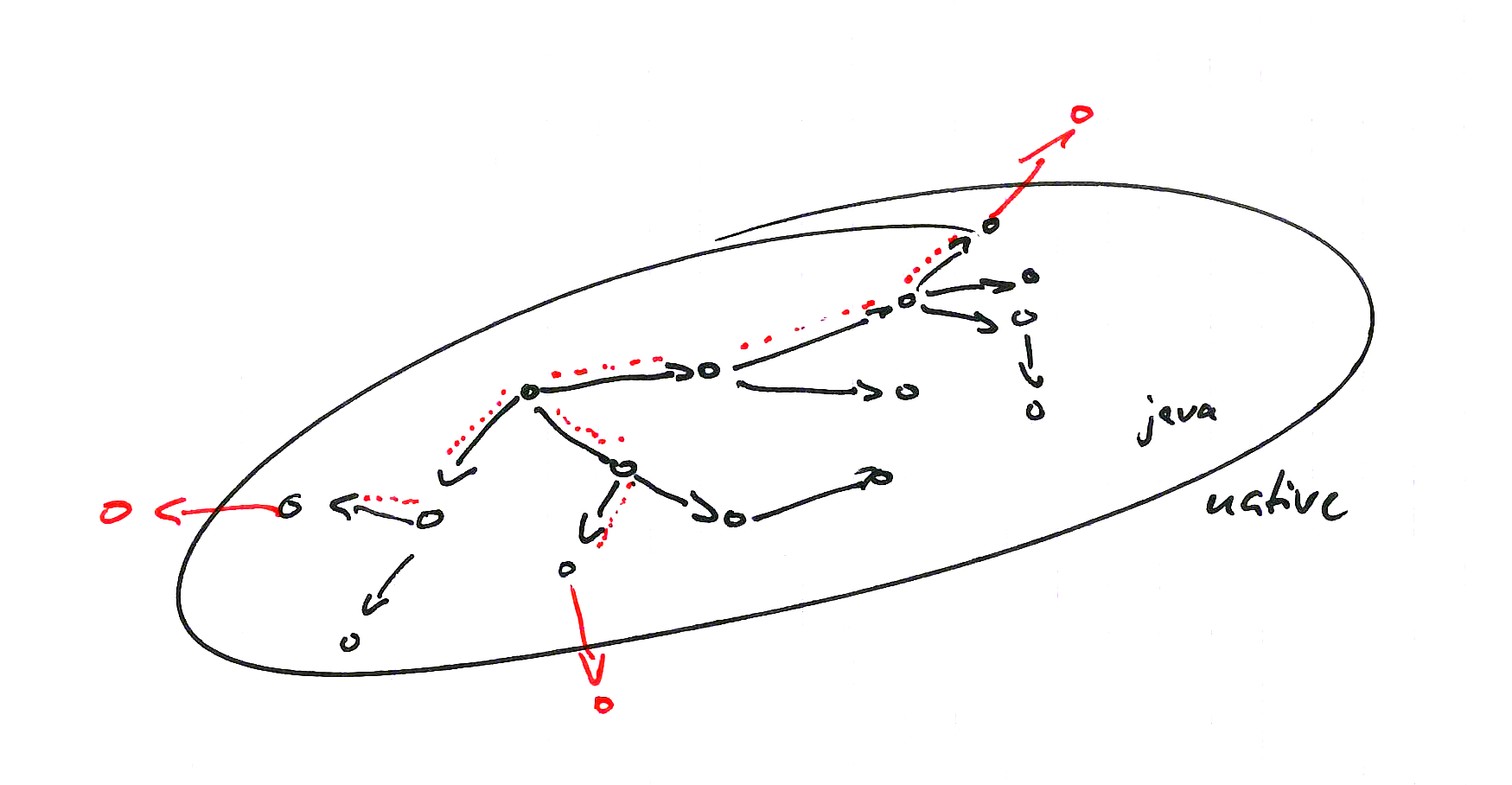
Static Calls
Through static calls you can construct a so called ambient resource. Capabilities can be shared between subjects that otherwise wouldn’t have access to it. You lose the ability to control the explicit dispensation of capabilities.
However, not every static call is harmful here. In certain circumstances functionally pure methods might be allowed.
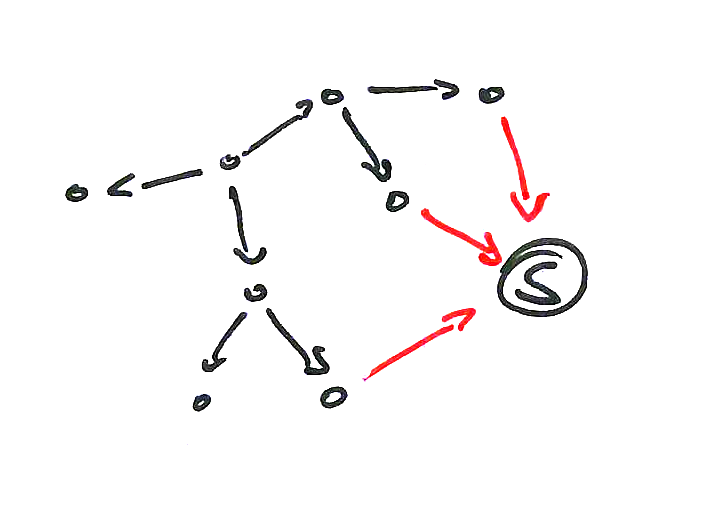
Intrusive Reflection
The most prominent and excessively used security feature of an object-oriented system is information hiding. If you break information hiding the inner state of an object can be read or altered. Subjects possessing a capability can use intrusive reflection to break information hiding and effectively gain all transitively accessible capabilities.
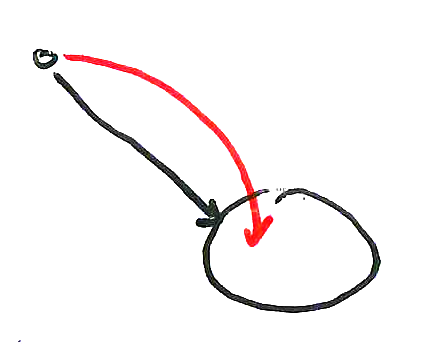
Native Calls
When using Java you might not be aware that most of the calls you make sooner or later end up executing code that is directly compiled from C/C++ to native code residing either in the Java Class Library or the software library you are currently using. This code is executed outside the security context of the Java Virtual Machine and can access and alter the VM memory directly. Thus, one of the major requirements of the OCaps model – the unforgeability of references – can not be guaranteed any more.
PEAKS is developed by the Security Subgroup of the Software Technology Group at Technische Universität Darmstadt
PEAKS was funded by the German Ministry of Education and Research (BMBF) (Reference no. 01IS12054) as part of the Softwarecampus initiative.